SAML Registration with Identity Providers
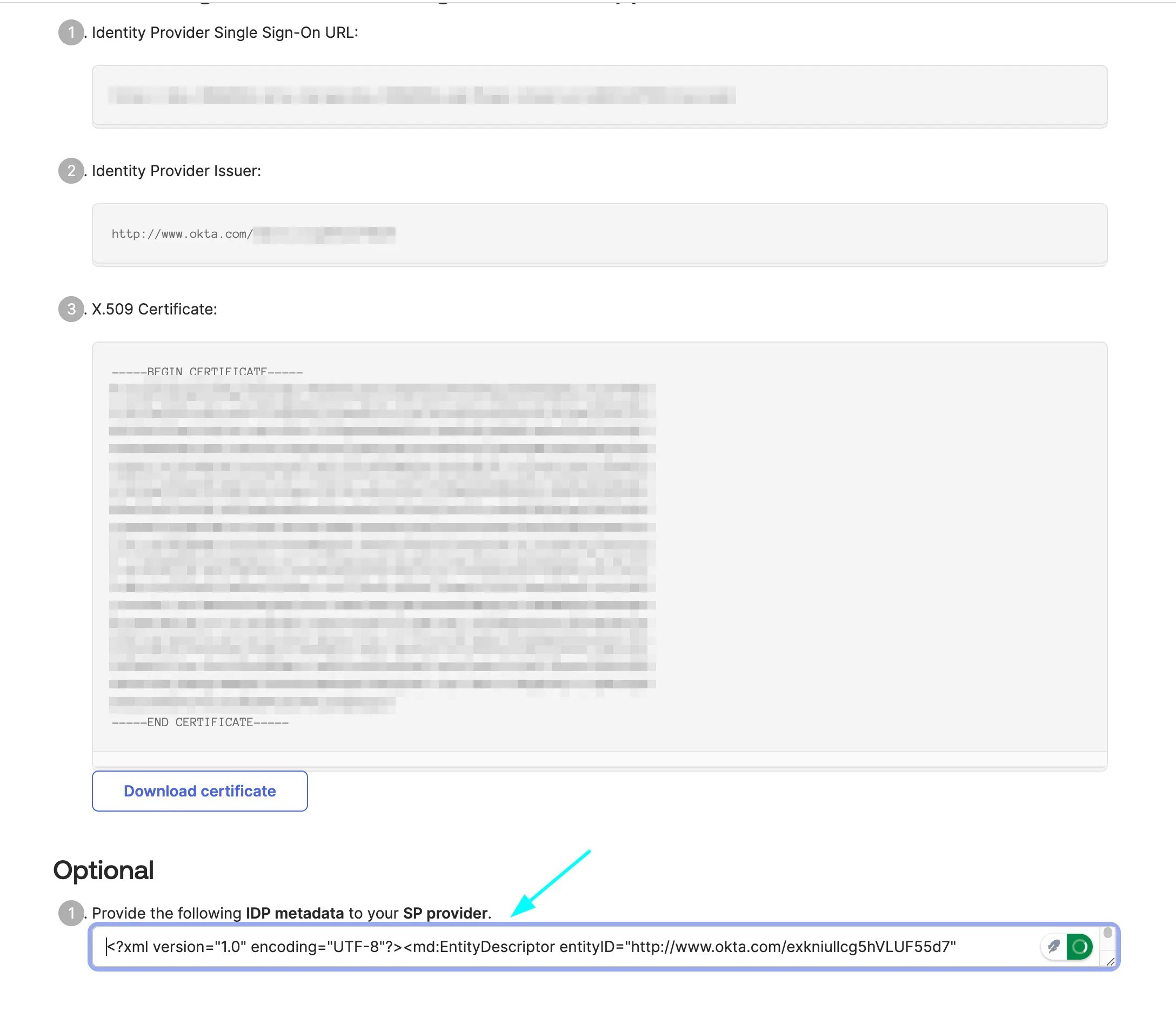
This guide explains the settings you need to use to configure SAML with your Identity Provider. Once configured, obtain an XML metadata file and use it to configure SAML in Formbricks.Note: Please do not add a trailing slash at the end of the URLs. Create them exactly as shown below.Assertion consumer service URL / Single Sign-On URL / Destination URL: https://app.formbricks.com/api/auth/saml/callback Entity ID / Identifier / Audience URI / Audience Restriction: https://saml.formbricks.com
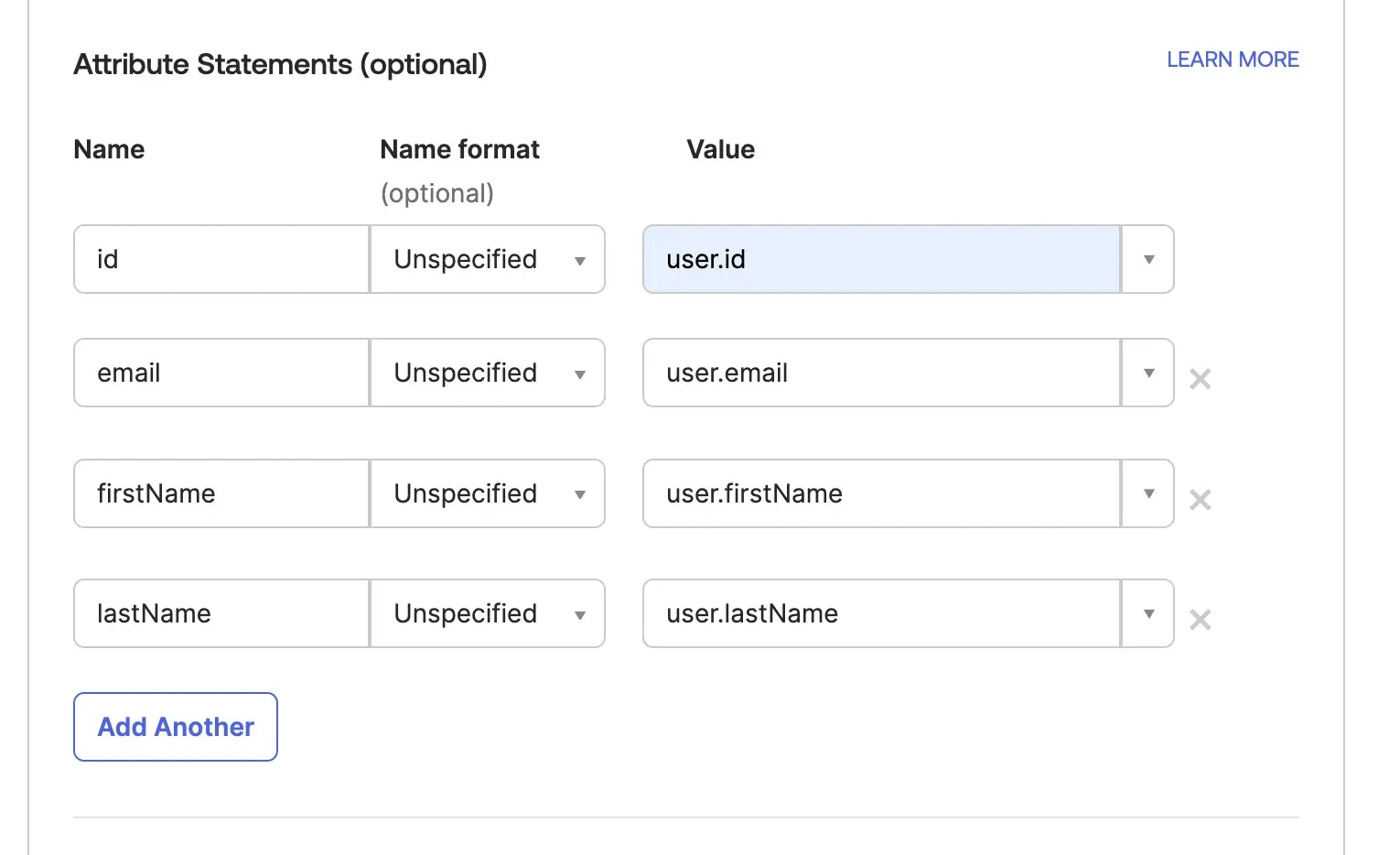
Note: https://saml.formbricks.com is hardcoded in Formbricks — do not replace it with your instance URL. It is the fixed SP Entity ID and must match exactly as shown in SAML assertions.Response: Signed Assertion Signature: Signed Signature Algorithm: RSA-SHA256 Assertion Encryption: Unencrypted NameID Format: EmailAddress Application username: email Mapping Attributes / Attribute Statements:
-
Name claim:
If your IdP has a
nameclaim, set the following claims to populate the name field:Many IdPs do not have aName Name Format Value name Basic user.name nameclaim. If not, you can use different claims to populate the name field. The order of precedence isname-> other options ->email. Other options:Refer to the table below for the different claims you can use for each IdP.Name Name Format Value firstName Basic FIRST_NAME_EQUIVALENT lastName Basic LAST_NAME_EQUIVALENT Above provided claims may differ based on your configuration and the IdP you are using. Please refer to the documentation of your IdP for the correct claims.IdP FIRST_NAME_EQUIVALENT LAST_NAME_EQUIVALENT Okta user.firstName user.lastName Microsoft Entra ID (Azure AD) user.givenName user.surname Google Workspace user.given_name / user.firstName user.family_name / user.lastName OneLogin user.FirstName / user.first_name user.LastName / user.last_name Auth0 user.given_name user.family_name JumpCloud user.firstname user.lastname
SAML With Okta
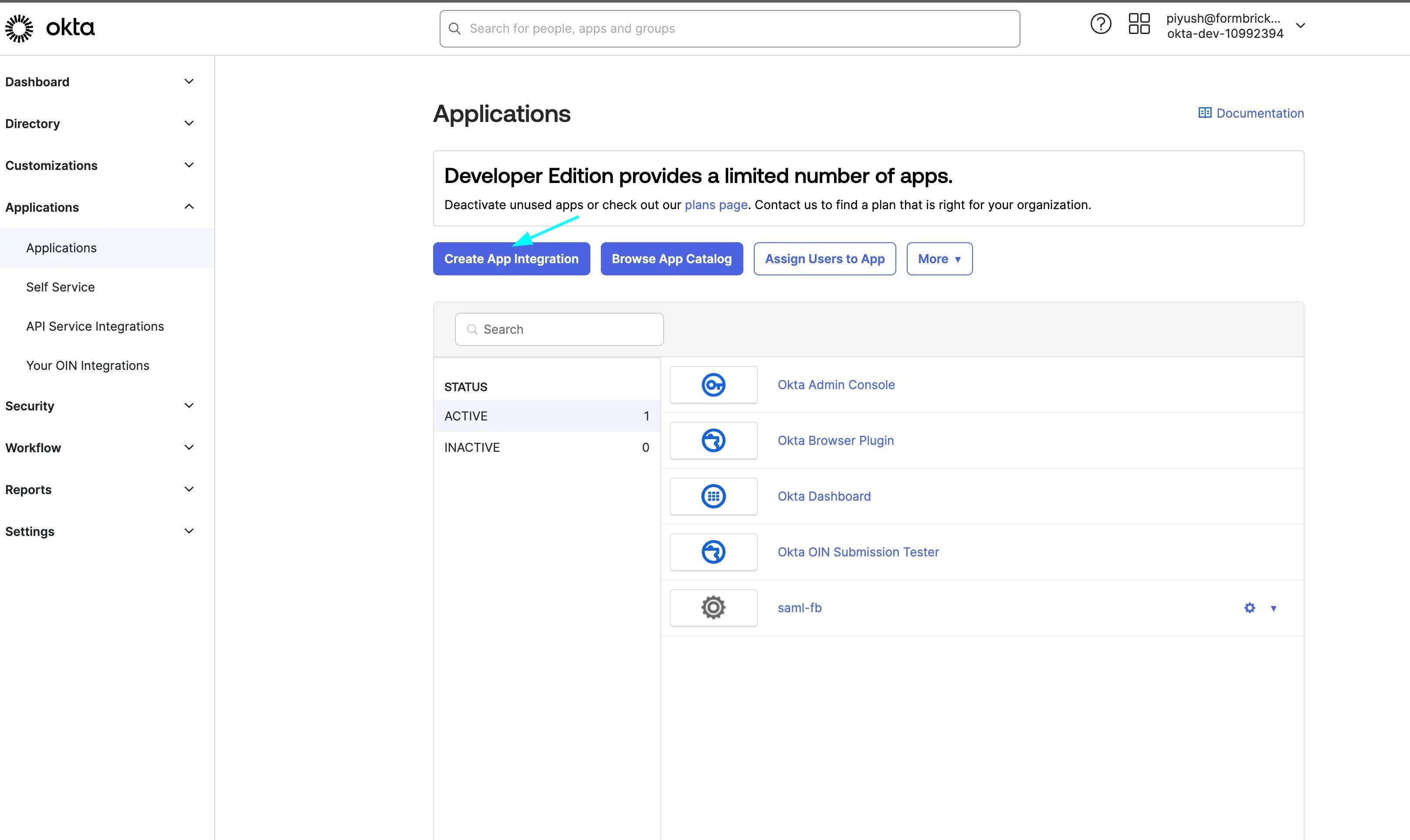
Create an application with your SAML provider
For example, in Okta, once you create an account, you can click on Applications on the sidebar menu:

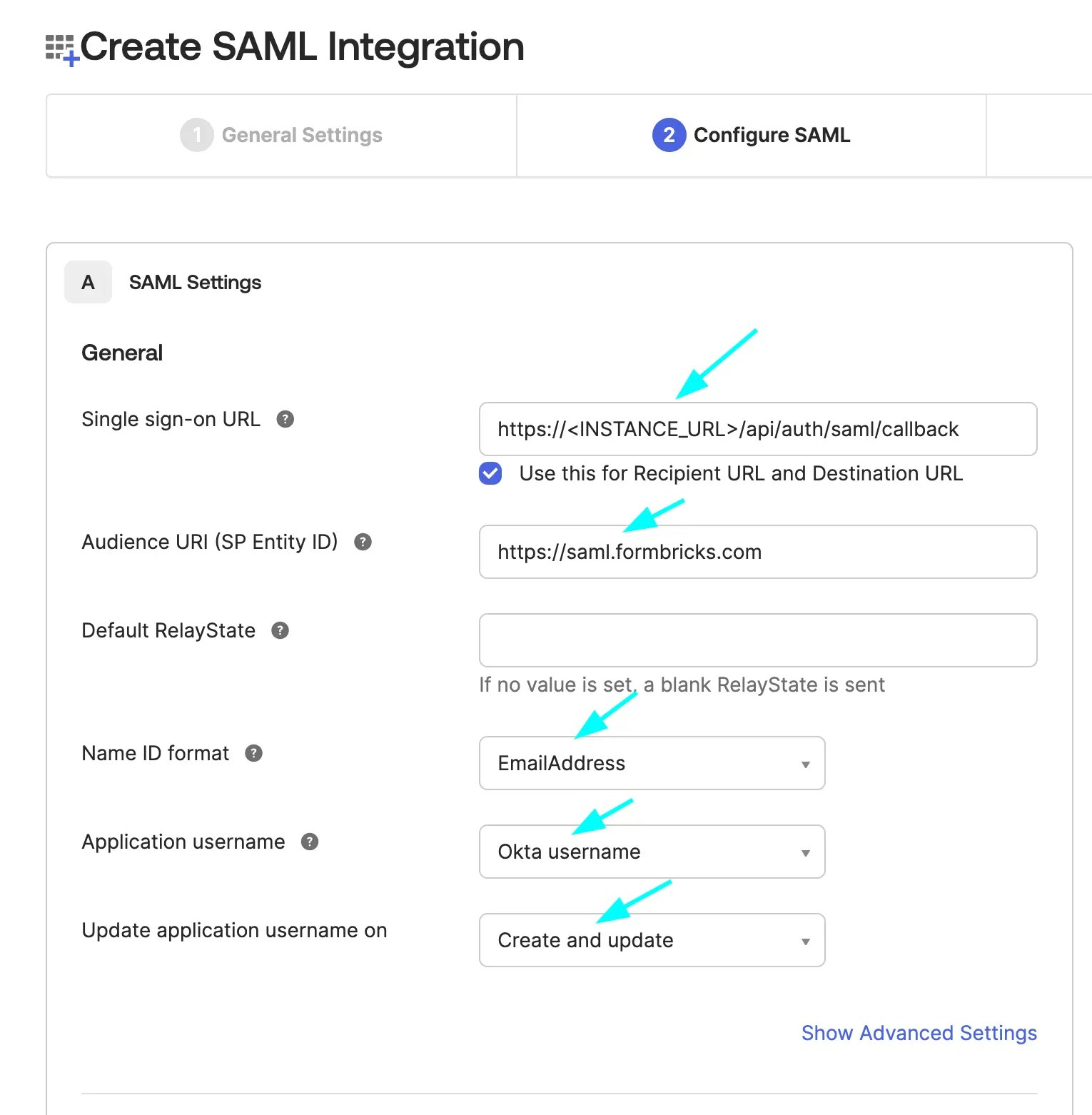
Enter the SAML Integration Settings as shown and click Next
- Single Sign-On URL:
https://<your-formbricks-instance>/api/auth/saml/callbackorhttp://localhost:3000/api/auth/saml/callback(if you are running Formbricks locally) - Audience URI (SP Entity ID):
https://saml.formbricks.com(hardcoded; do not replace with your instance URL)